How Connected uses customer-managed encryption keys
When Connected protects data using customer-managed encryption keys, it encrypts and decrypts all data using a sequence of encryptions with the appropriate customer, user, and workspace keys. The following figure illustrates this process.
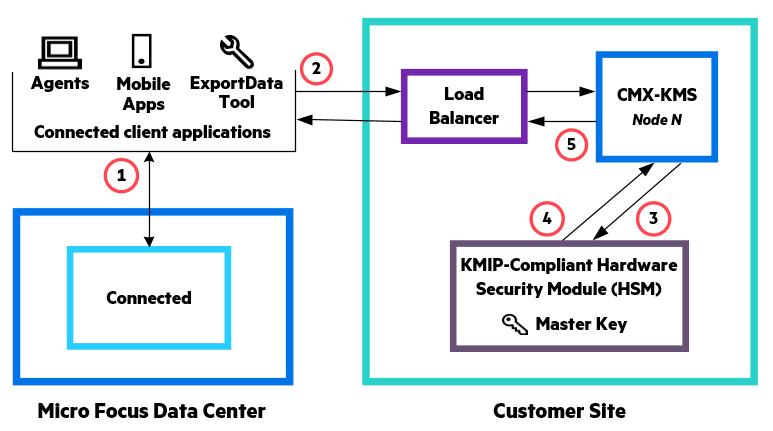
- When a Connected client application starts, it requests from Connected the URL to Connected Key Management Server (CMX-KMS) and the encrypted customer, user, and workspace keys.
- If the Connected client application does not have a cached decrypted copy of the user's workspace key when it attempts to encrypt or decrypt the user's data, it sends CMX-KMS the encrypted customer, user, and workspace keys and requests a decrypted workspace key.
- CMX-KMS requests that the hardware security module (HSM) decrypt the customer key.
- The HSM decrypts the customer key using the site's master encryption key and returns the decrypted key to CMX-KMS.
-
CMX-KMS uses the decrypted customer key to decrypt the user key that it then uses to decrypt the workspace key. It returns the decrypted workspace key to the client application.
The client application uses the decrypted workspace key to encrypt or decrypt the user's data and then temporarily caches the decrypted key for possible use in the near future. When the cache expires, the key is deleted. Any subsequent need to encrypt or decrypt user data requires the application to repeat steps 2 through 5.