Creation of a user workspace encryption key
Connected organizes the various categories of a user's data into distinct user-specific workspaces. For backup data, each of a user's protected device has its own workspace. Distinct user workspace keys encrypt the data stored in each of a user's workspaces. The following figure illustrates the creation of a user workspace key.
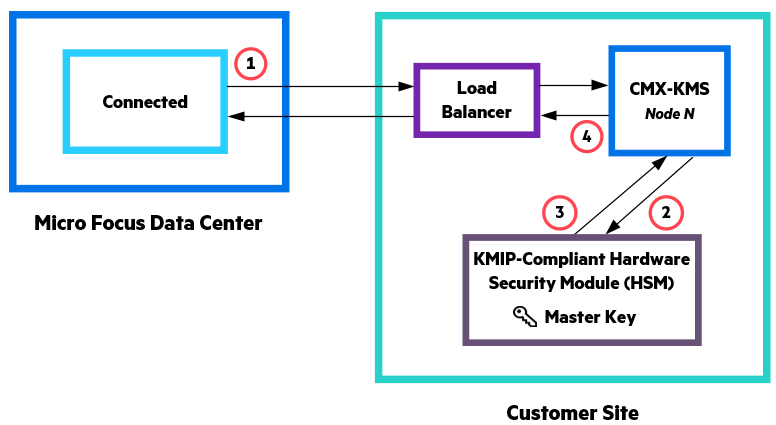
- Connected sends the encrypted customer and user keys to Connected Key Management Server (CMX-KMS) and requests an encrypted workspace key.
- CMX-KMS requests that the hardware security module (HSM) decrypt the customer key.
- The HSM decrypts the customer key using the site's master encryption key and returns the decrypted key to CMX-KMS.
- CMX-KMS uses the decrypted customer key to decrypt the user key. It then creates a workspace key and encrypts it with the user key. It returns the encrypted workspace key to Connected, which stores it for future use.